FTK Lite Imaging of a physical drive Using FTK Imager lite, it was determined a live image of the physical system disk resulted in an image with an encrypted bitlocker container on it Note that the phrase "physical" here corresponds directly with FTK Imagers use of the term in their image acquire menu Imaging of a logical partition FTK Imager Lite is a standalone executable which can be run using, for example, a USB This is preferred, as unnecessary installations on the targeted system will further contaminate the evidence An important aspect is to also dump out the volatile data to an external device with enough storage Open Windows Explorer and navigate to the FTK Imager Lite folder within the external HDD Run FTK Imagerexe as an administrator (right click > Run as administrator)

Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna
Ftk imager lite command line
Ftk imager lite command line-The FTK Imager has the ability to save an image of a hard disk in one file or in segments that may be later reconstructed It calculates MD5 hash values and confirms the integrity of the data before closing the files In addition to the FTK Imager tool can mount devices (eg, drives) and recover deleted files PreRequisite FTK Imager Lesson Forensic Report SampleVolatile Memory Acquisition using FTK Imager Lite This is a sample forensic report of Volatile Memory using the tool " FTK Imager Lite by AccessData " This procedure is used by investigating agencies to log each step in evidence acquisition process, and the report is presented in the court for the hearing




Using Ftk Imager On Cli Challenging New Disks Technologies Cybrary
There are many tools that can capture the memory from a live system, but we will be using FTK Imager Lite from AccessData It is a GUI tool and compared to some other similarly purposed commandline tools, it leaves a larger footprint on the machine; There is no boot to BIOS/UFEI So I've had to boot to Windows (81 I think) but I can't run FTK Imager lite or command line because they are not signed by Microsoft and the exe's wont run I found a ddexe to try, but same as above again Does anybody know or any tools that I can use to get an image of this 32GB eMMC (Chip off is not an optionIf you Google it, it will show you what feature you need to turn off in windows It's not ftk imager related 5 level 1 sheepdog11 10 months ago It's a common FTK imager lite issue with Windows 10 machines Switch to FTK imager 43 (not lite use the portable version), and it'll work There's a howto on access data's website
FTK Imager CLI for Mac OS AccessData Command line Mac OS version of AccessData's FTK Imager IORegInfo Blackbag Technologies Lists items connected to the computer (eg, SATA, USB and FireWire Drives, software RAID sets) Can locate partition information, including sizes, types, and the bus to which the device is connected Mac Memory Reader FTK Imager permits digital forensic professionals to create an image of a local hard drive AccessData's FTK Imager allows the examiner to create both local and remote images When a disk image is acquired locally, it indicates that the data storage device such as a hard drive on a system is physically accessible Listing drives with FTK Imager CLI I recommend that you make completely sure which is the target disk to get the image The best way to do it is by running the fdisk
It tells us how to use FTK Imager command line for creating the hash of the hard disk More Views 4,9 Related Posted In Software s computer forensics, cybersecurity, DFIR, digital forensics, digital forensics software, digital image forensics, forensic imaging, FTK Imager, incident response, windows 10 forensics, windows forensics One of my favorite tools to image with is the FTK Imager command line program It is a lightweight, fast, and efficient means to extract the image from your suspect drive You can run the CMD line program on any operating system with very little difference in syntax but I will be focusing on the Linux version that comes with SIFTIn this video we will use FTK Imager to create a physical disk image of a suspect drive connected to our forensic workstation via a write blocker FTK Imager




Pdf Impact Of Tools On The Acquisition Of Ram Memory



Windows Registry Extraction With Ftk Imager Free Tutorial
Make A Copy Of Folder Command Line Images!Simple art pictures Download free images, photos, pictures, wallpaper and use itThe ftk imager can command line utility can be downloaded from the access data's webpage At the time of this writing, the link was the latest v ersion of ftk imager command line utility



Windows Registry Extraction With Ftk Imager Free Tutorial



Ftk Imager Lite Lesson 2 Create Ftk Imager Lite Iso With Winiso
A screen shot of the icon can be seen below and once it is open you should be greeted with the FTK Imager dashboard FTK Imager version Release Date Download Page FTK Imager version Release Date Download Page FTK Imager version Release Date Download Page FTK Imager Lite version Release Date Download PageU Suspect Command Line and parameters used u Start Time Information Vs Boot Time u Security Identifiers (SIDs) MFT –Master File Table u NTFS u FTK Imager Lite to copy locked files u Psloglist (sysinternals) u Memory Forensics u Volatility Plugin evtlogs(xp/03 only)Make FTK Imager launch from USB Go to AccessData and download the latest version of FTK imager Install FTK imager to your system Copy the dynamic link libraries (dll files) and the FTK Imager application file to a USB drive The used space on the USB drive should be around 71 MB FTK imager bootable USB Acquire RAM & Pagefile from Windows



Windows Registry Extraction With Ftk Imager Free Tutorial



Introduction To Computer Forensics Ftk Imager Lite Creating An Image File Youtube
FTK Imager has been around for years but it wasn't until recently that AccessData released a break out version for use on the Command Line for the general public Or maybe I was just unaware of it They've made these command line tools freely available to the general public as well as multiplatform (Windows, Debian, RedHat, and Mac OS)Download Ftk Imager For Mac Manual Magazine free and unlimited AccessData provides digital forensics software solutions for law enforcement by E Colloton — There is a command line version of FTK Imager available for macOS;In this video we will show how to use FTK Imager command line version on Windows 10 to create a hash of a physical disk We show how to add FTK Imager comman




Practical Approaches For Reappraisal Weeding And Deaccessioning Ppt Download




Comprehensive Guide On Ftk Imager
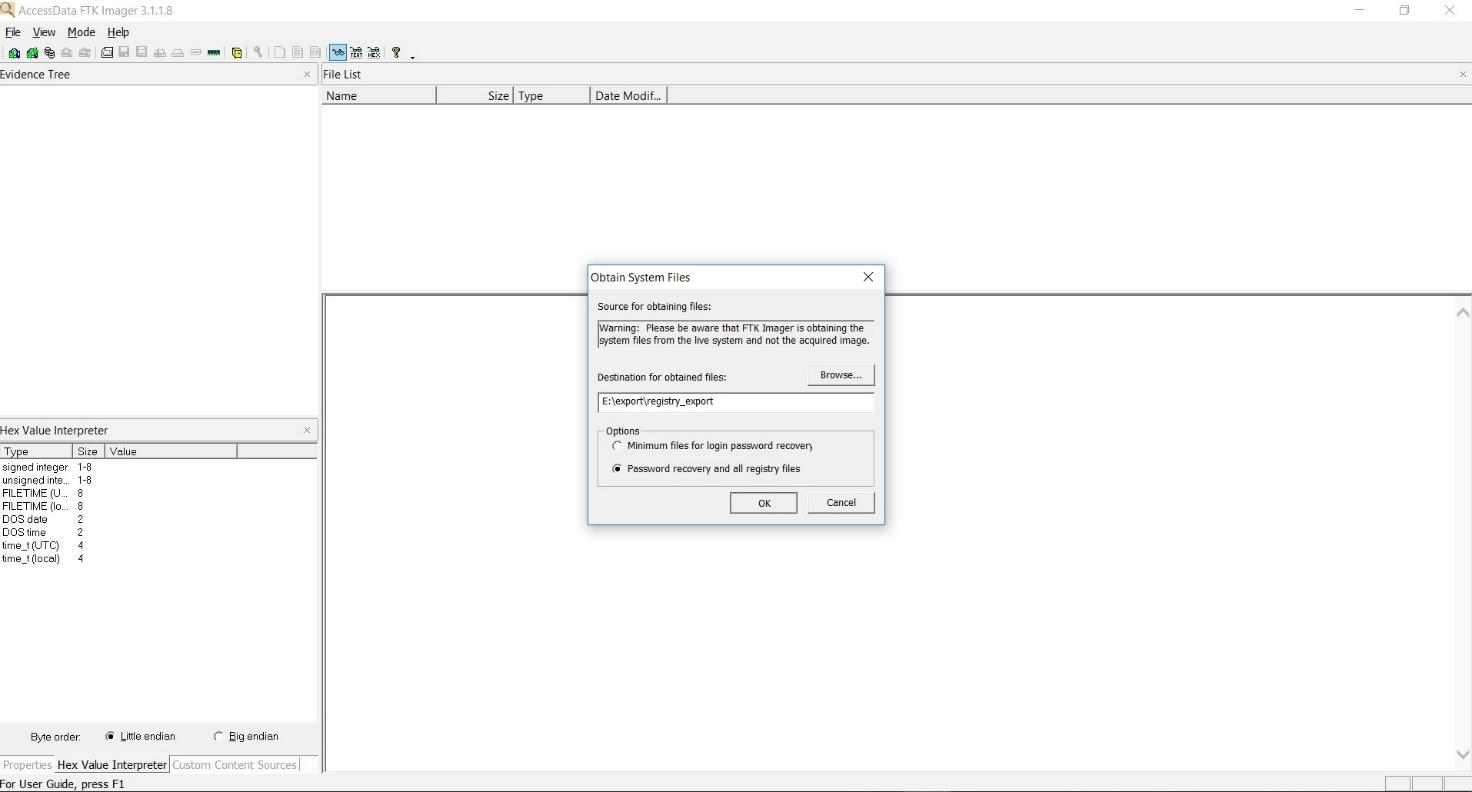
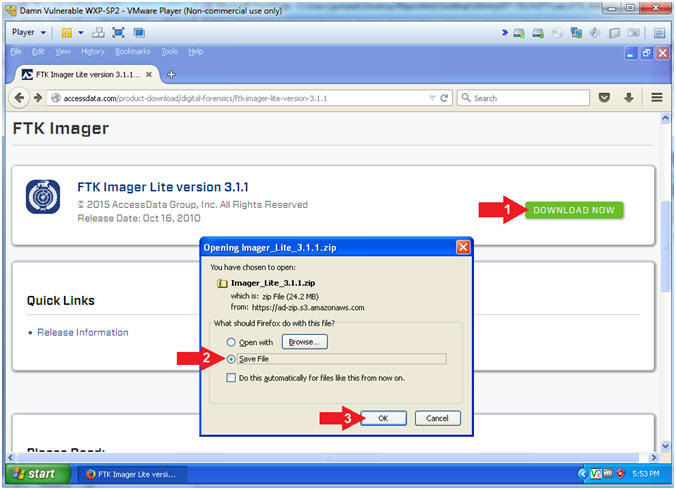
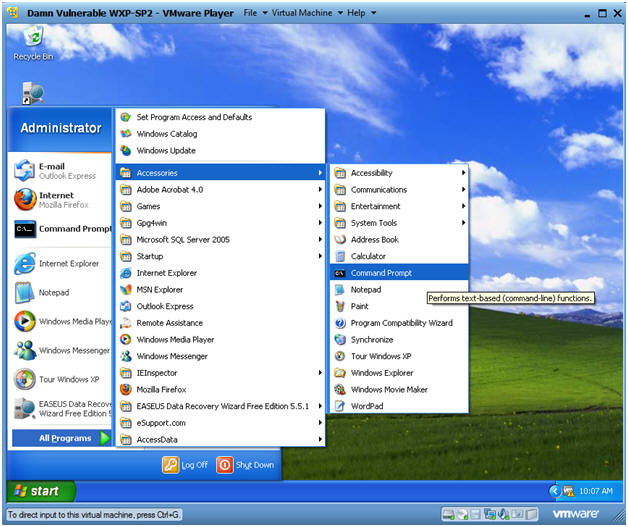
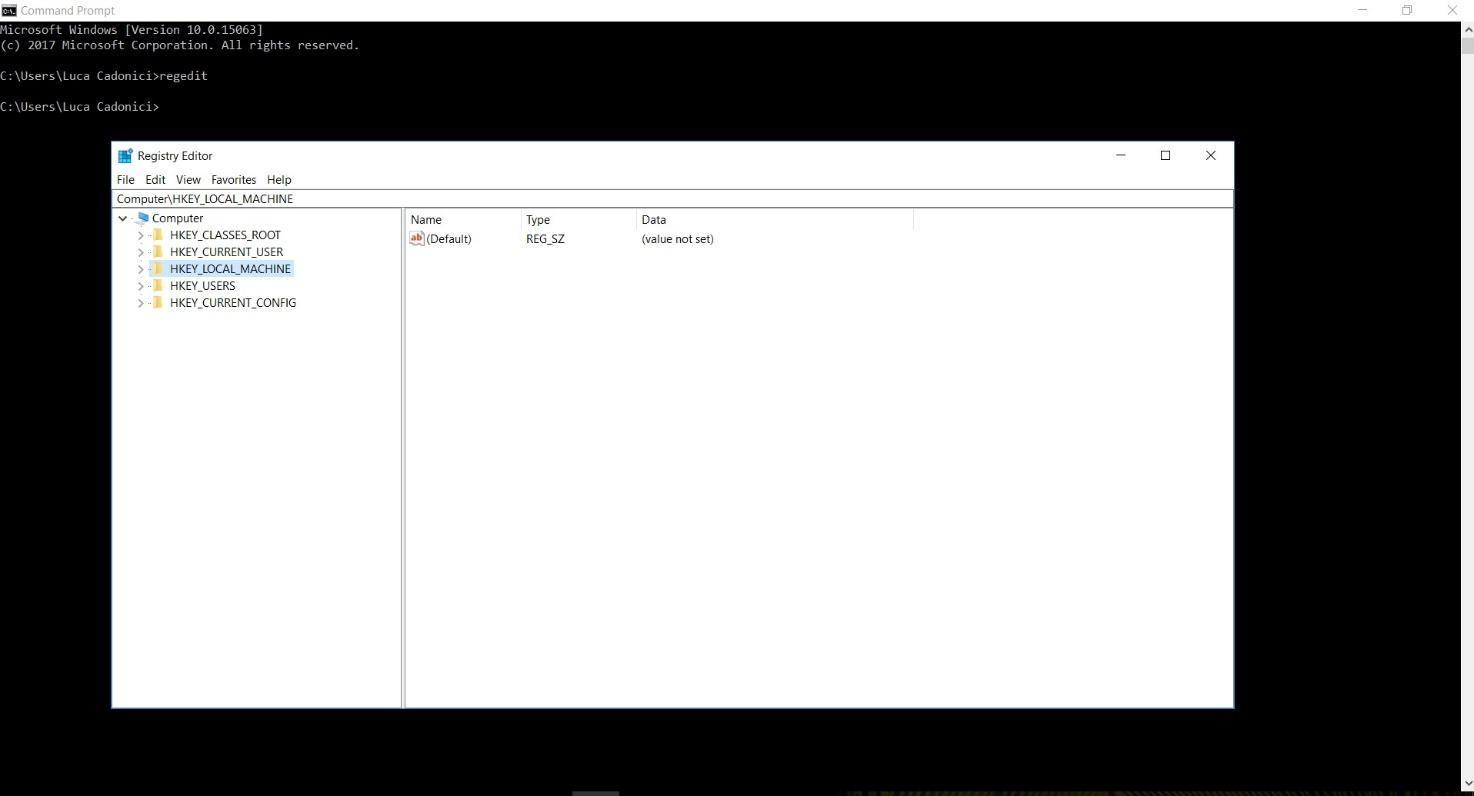
2 Start FTK Imager From Your Windows PC On your Windows PC, doubleclick the icon labelled "AccessData FTK Imager" FTK Imager will start 3 Add Physical Drive As Evidence Item ("File" > "Add Evidence Item") Click on "File" and select "Add Evidence Item" to select our physical drive in the next step 4 FTK Imager Lite will then export all the registry hives from the live system to the target location selected by the examiner Open the target location and ensure the files exist Open the registry hives with a known good utility (such as regedit) to confirm they are readableRightclick the "Imager_Lite_311zip" file and click "Extract All In the 'Extract Compressed (Zipped) Folders" box, clck Extract In the "Imager_Lite_311" window, doubleclick FTK_Imagerexe



Ftk Imager Lite Version 3 1 1 Download




Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna
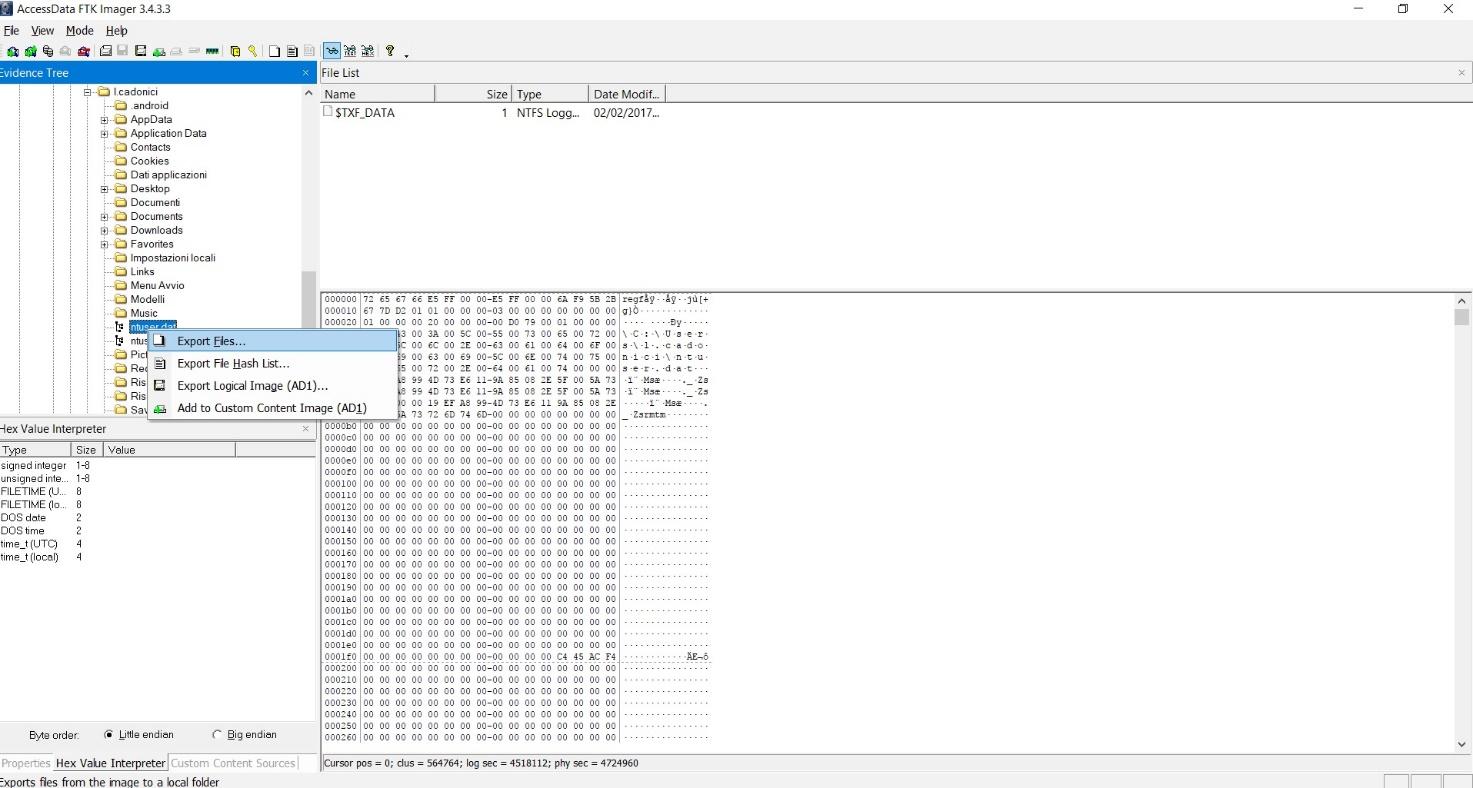
A hive exported using the "reg save " command (top) and the FTK Imager Lite tool (bottom) Note the "expected" file size 0x02c000 (hive bins data size) 4096 (base block) = bytes"Great speed improvements with FTK Imager 43, particularly with the verification of multiple images No longer a need to batch verify multiple images via the command line, as the GUI is able to prioritize and process in parallel without an adverse impact upon performance" SeeThere are many tools that can capture the memory from a live system, but we will be using FTK Imager Lite from AccessData It is a GUI tool and compared to some other similarly purposed commandline tools, it leaves a slightly larger footprint on the machine;




Using Ftk Imager On Cli Challenging New Disks Technologies Cybrary




Ftk Imager For Mac Dressusa
It might be worth posting the output here for others to check over Step 1 Download and install the FTK imager on your machine Step 2 Click and open the FTK Imager, once it is installed You should be greeted with the FTK Imager dashboard Step 3 In the menu navigation bar, you need to click on the File tab which will give you a dropdown, like given in the image below, just click on the first one that says Using FTK Imager Lite Command Line The Options As with nearly all programs in Linux there is a help file that allows the user to see what options are



Ftk Imager Lite Lesson 1 Create Ftk Imager Lite Iso With Doiso




How To Use Ftk Imager To Recover Data 1337pwn
You should also learn and realize that not every image will be encrypted, so when you try to verify an image that was created with FTK Imager, you can just use the standard commands and verify the image C\FTK ImagerCLI 290_Win32\FTKImager> ftkimagerexe c\temp\imageftkimagerE01 verify Verifying imageConnect the external HDD into the target system that has FTK Imager Command Line folder residing After starting FTKImager you are greeted with the main window Open the menu " F ile" ( ALTF ) and choose the option "Cap t ure Memory" ( ALTT ) Chose a Destination for your image, always chose an external path like a USBDrive or External HDD



Ftkimagerug Imager 2 9 0 User Guide




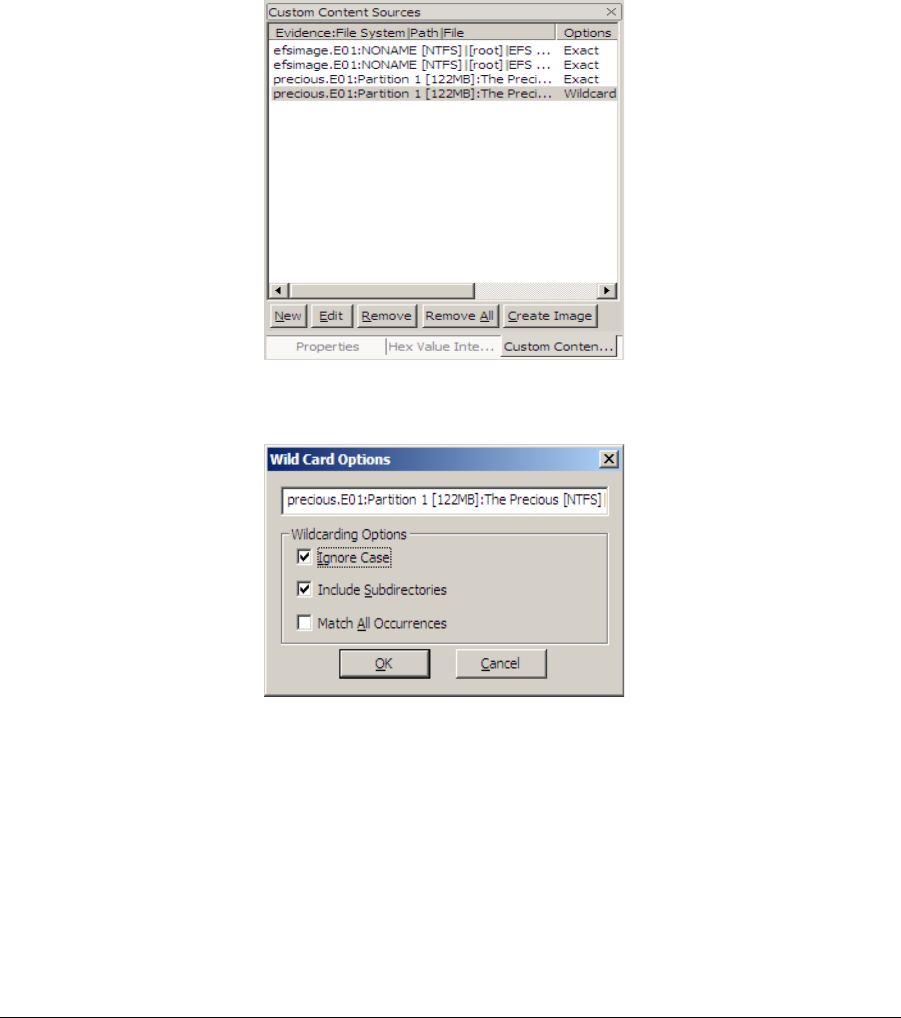
Ftk Imager And Custom Content Images Salt Forensics
FTK ® Imager 311 FTK ® Imager is a data preview and imaging tool used to acquire data (evidence) in a forensically sound manner by creating copies of data without making changes to the original evidence After you create an image of the data, use Forensic Toolkit® (FTK®) to perform a thorough forensic examination and create a report of your findingsPosted (4 days ago) Using command line FTK Imager (for 32 bit Windows System) If you are trying to image 32 bit Windows System, you will need to use FTK Imager Command Line Login with a local admin account on the target system;Memory and Live Acquisition FTK Imager Lite FTK Imager Lite is a GUIbased software to acquire physical disk images On running Windows systems it also supports the acquisition of memory and logical system images including registry, event logs and alike FTK Imager Lite is free but a registration is required



Windows Registry Extraction With Ftk Imager Free Tutorial



Project 3 Capturing A Ram Image 15 Points
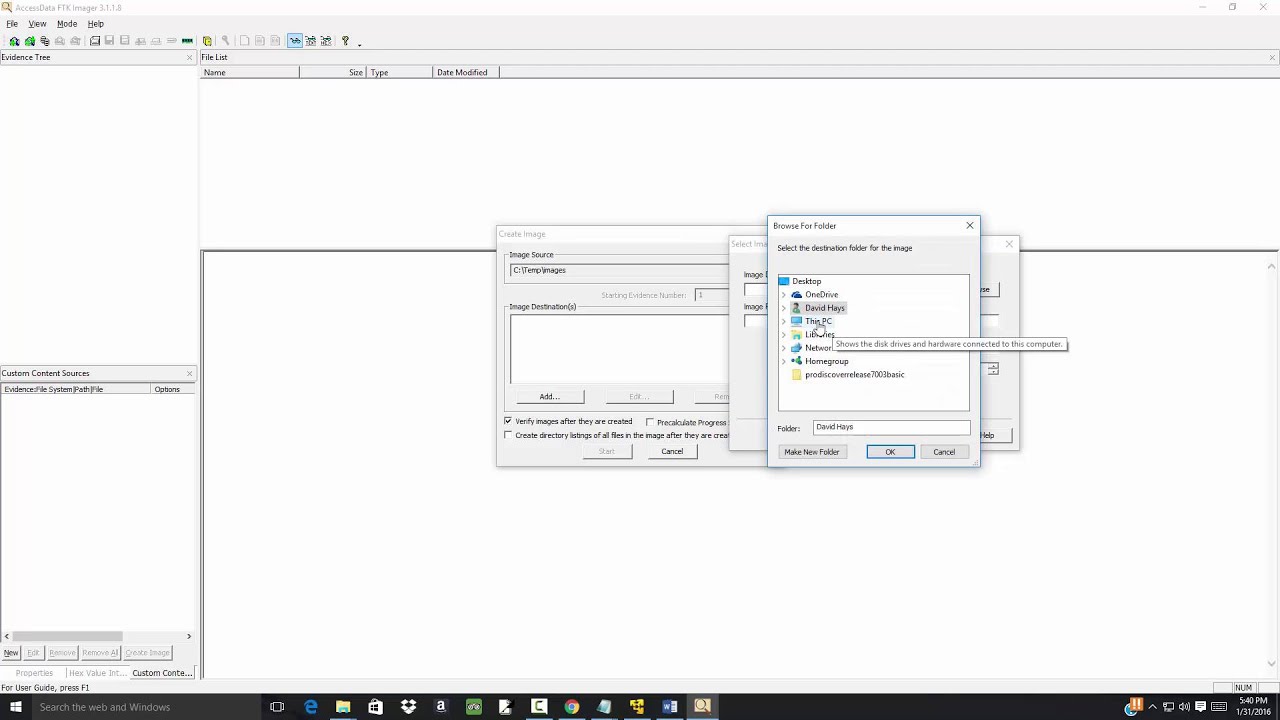
Created using EnCase Imager, FTK Imager, FTK Imager Lite, GetData Forensic Explorer Imager, Magnet Acquire, Timdd (a command line version of TIM used for forensic product testing), and X In this example I use FTK Imager 3146 to find a picture (JPEG file) in Windows 7 STARTING FTK IMAGER Open the Physical Drive of my computer in FTK Imager The contents of the Physical Drive appear in the Evidence Tree Pane Click the root of the file system and several files are listed in the File List Pane, notice the MFT Blogger Josh Lowery's opinion, in a blog post titled "Installing FTK Imager Lite in Linux Command Line", concurs with Muir's view as well The Computer Forensics Analyst based out of NYC, says he prefers FTK since it is a "lightweight, fast, and efficient means to extract the image from your suspect drive"
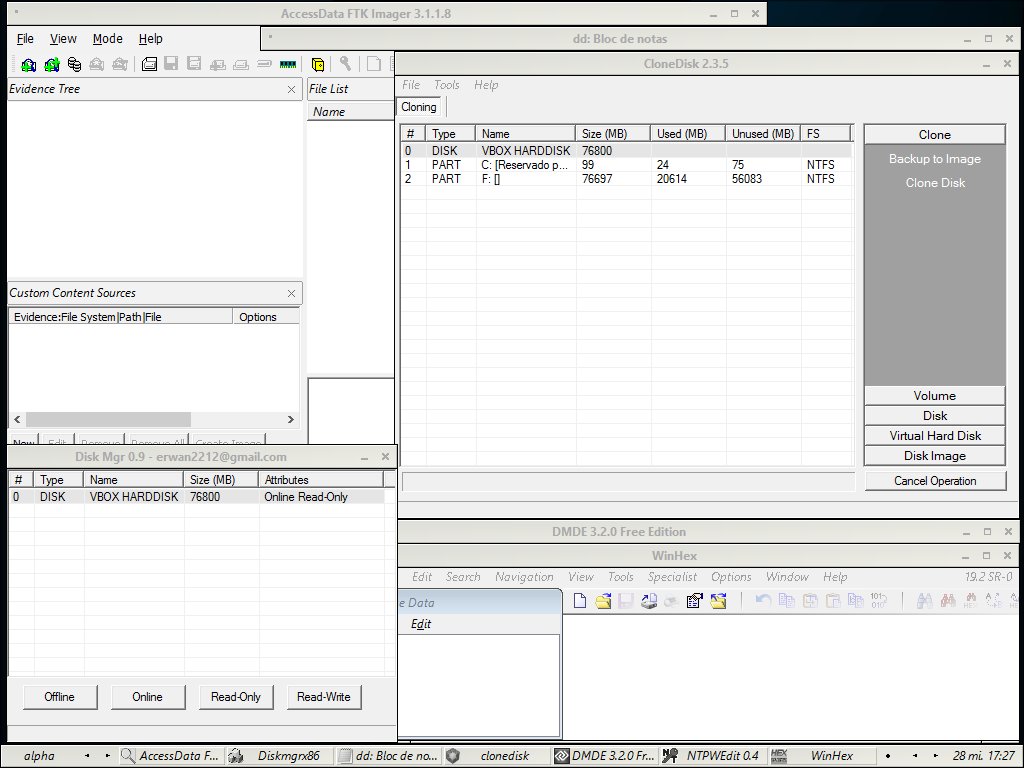



Windows Forensic Environment Winfe Beta En Follow The White Rabbit




Using Ftk Imager On Cli Challenging New Disks Technologies Cybrary
Great post There are few things more frustrating than Windows denying access to a file you need Two other options are AccessData's FTK Imager Lite (from a thumbdrive) and FResponse (if you are working remotely) It is nice to have options! When trying to use FTK Imager to collect Memory, Imager crashes or the computer "blue screens" and must be rebooted Resolution Enter the bios of the machine and look for any setting relating to virtualization and disable it In Award Bios it is usually found under Advanced Chipset Settings It can sometimes be called "VT," "VTX," or "AMDV"FTK Imager Lite version 311 Release Date Download Page Forensic Toolkit® (FTK®) Forensic Toolkit (FTK) version 63 Release Command Line Versions of FTK Imager Windows 32bit – 311 Release Date Download




Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna




Ftk Imager For Mac Os X Greatvin
1 First, open FTK Imager and navigate to Image Mounting 2 After that, choose the E01 image that a user want to mount 3 Now, click on Mount button and see with which physical drive the image is mapped 4 Then, create a new folder and open command prompt as administrator 5 Type cProgram FilesOracleVirtualBox and press Enter 6FTK Imager Lite is a GUI based tool that can also be run from a USB drive, just unzip the download file and doubleclick the"FTK Imagerexe" file FTK Imager Lite has a larger footprint and does much more than acquiring memory images, this tool is a reduced version of AccessData's full forensic software package and has numerous capabilities Utah Office 603 East Timpanogos Circle Building H, Floor 2, Suite 2300 Orem, UT



2



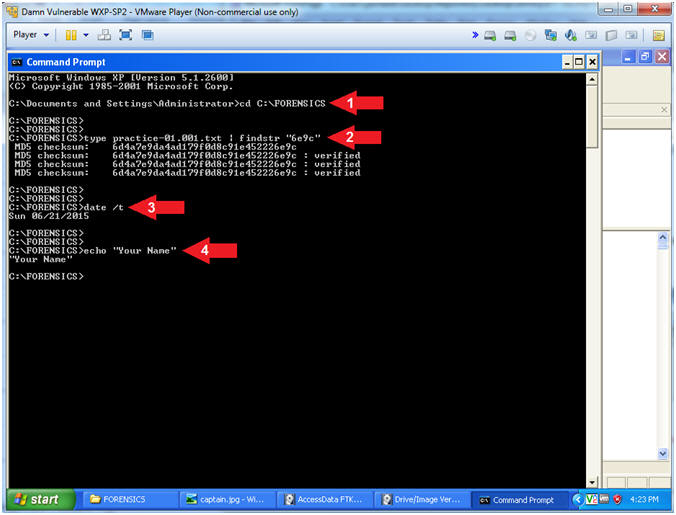
Project 3 Capturing A Ram Image 15 Points
FTK Imager CLI for Mac OS* AccessData Command line Mac OS version of AccessData's FTK Imager IORegInfo Blackbag Technologies Lists items connected to the computer (eg, SATA, USB and FireWire Drives, software RAID sets) Can locate partition information, including sizes, types, and the bus to which the device is connected Mac MemoryHowever, all considering, its impact on the system is still rather minimal andIt is not necessary to use DoISO to burn FTK Imager Lite to an ISO You can use Nero, Roxio, or whatever However, DoISO is free and good Instructions Start > All Programs > DoISO > DoISO Browse For Folder Instructions Select the Create ISO Tab Click the Blue Circle



Ftk Imager Lesson 4 Mount Image File Recover Deleted File



Ftk Imager Lite Lesson 2 Create Ftk Imager Lite Iso With Winiso
"YPrograms\FTK Imager Lite\FTK Imagerexe The application has failed to start because its sidebyside configuration is incorrect Please see the application event log or use the commandline sxstraceexe tool for more detail" Does the event log reveal anything of use?However, all considering, its impact on the system is still rather minimal and it tends Its capabilities are vast and are similar to Page 3 Cervellone 3 of 30 those of FTK® and EnCase® Forensic, however, due to its opensource nature and heavy reliance on the Linux Terminal and command line, it is advised that only an examiner highly skilled in Linux use the SIFT Workstation for casework



Ftk Imager Lite 3 1 1 Computerforensics




Exporting Registry Hives From A Live System My Dfir Blog



Ftk Imager Lite Lesson 1 Create Ftk Imager Lite Iso With Doiso




August 14 Free Android Forensics



Forensic Report Sample Volatile Memory Acquisition Using Ftk Imager Lite By Vishal Thakur Medium



2




4n6k 18



2



Ftkimagerug Imager 2 9 0 User Guide




鑒真數位 Ftk Imager Lite在mac上進行映像檔製作 相信使用過免付費軟體ftk Imager Lite 的人都知道它是個很不錯的工具 但可能鮮少人知道它還有mac及linux的版本 在此為各位介紹mac版的ftk Imager Lite 先打開瀏覽器訪問accessdata的官網 下載ftk Imager的command




Ftk Imager Lite Tutorial Youtube




Ftk Imager Lite Mayfasr
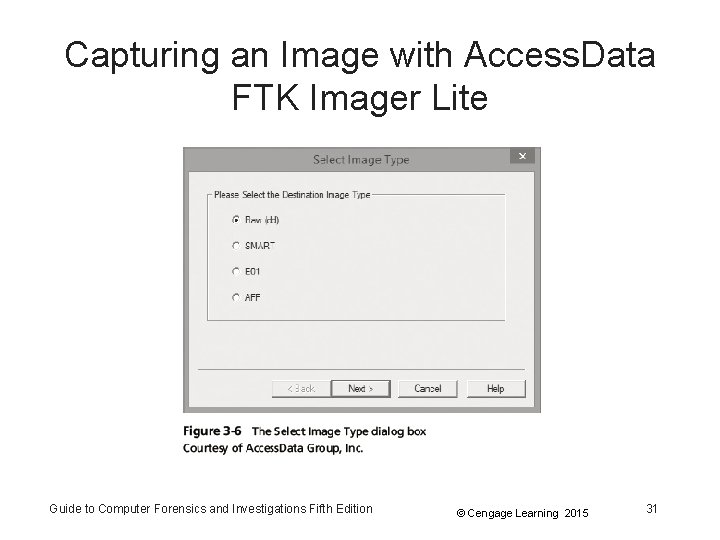



Guide To Computer Forensics And Investigations Fifth Edition




Using Ftk Imager On Cli Challenging New Disks Technologies Cybrary
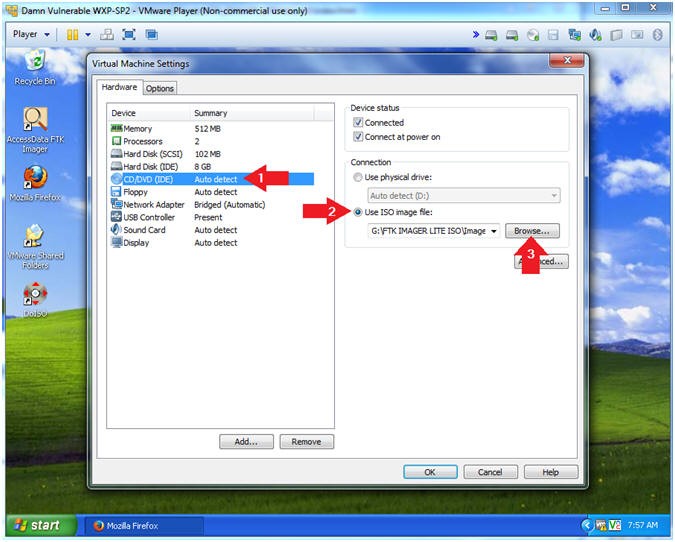



Ftk Imager Lite Lesson 1 Create Ftk Imager Lite Iso With Doiso



2




Using Ftk Imager To Create A Disk Image Of A Local Hard Drive 1337pwn




Computer Forensics For Everyone Installing Ftk Imager Lite In Linux Command Line
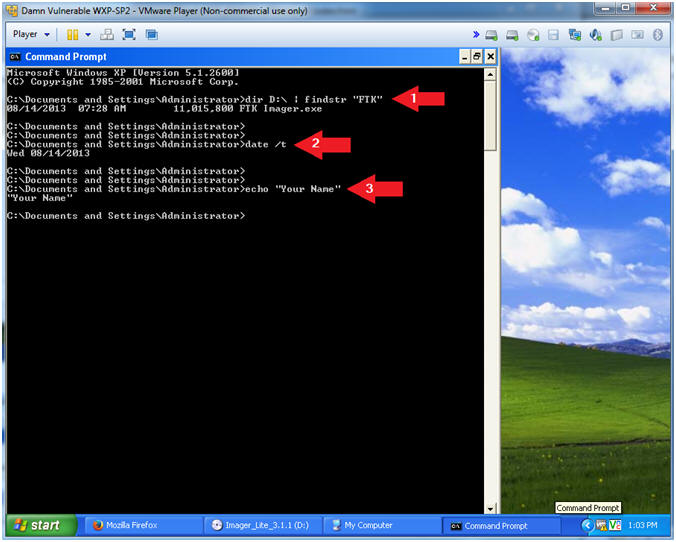



Ftk Imager Lite Lesson 2 Create Ftk Imager Lite Iso With Winiso



Ftk Imager For Mac Manual Smoothsoftis




Computer Forensics For Everyone Installing Ftk Imager Lite In Linux Command Line




Ftk Imager For Mac



2




Forensic Report Sample Volatile Memory Acquisition Using Ftk Imager Lite By Vishal Thakur Medium




Digitalresidue S Forensics Memory Acquisitions Memoryze Ftk Imager Sleuthkit Etc



2




4n6k 18




Using Ftk Imager On Cli Challenging New Disks Technologies Cybrary
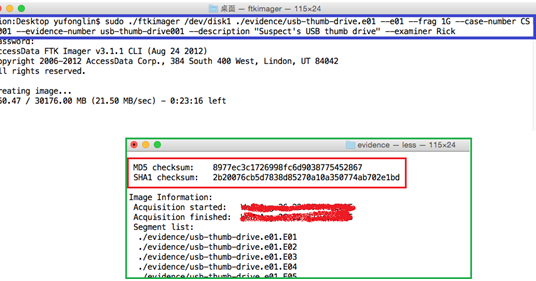



Ftk Imager For Mac Dressusa




Ftkimagerug Imager 2 9 0 User Guide




Comprehensive Guide On Ftk Imager




How To Guide Image A Hard Disk Using Ftk Imager Pdf Free Download




Ftk Imager Eforensics Mag Rebranded Final Aug14 Pdf Computer Forensics Digital Forensics



2



Ftk Imager Lite Lesson 2 Create Ftk Imager Lite Iso With Winiso



2



2



Project 17 Capturing And Examining The Registry 30 Pts



Ftk Imager For Mac Os X Greatvin



2




Ftk Imaging Step By Step By Parves Kamal Issuu




Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna
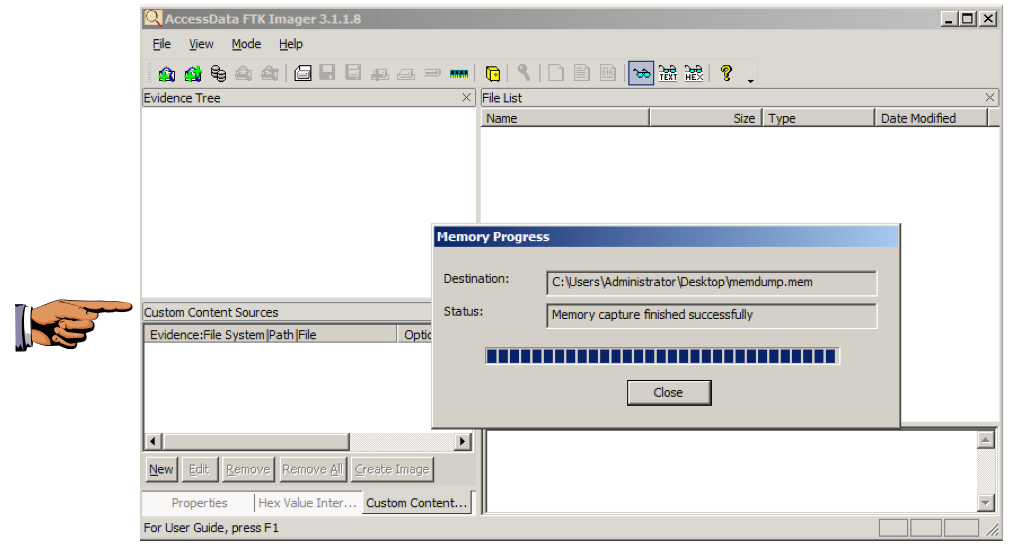



Project 3 Capturing A Ram Image 15 Points



2



2




How To Capture Ram With Forensic Tool Kit Strings And Photorec Tophack Io




Digitalresidue S Forensics Memory Acquisitions Memoryze Ftk Imager Sleuthkit Etc




Computer Forensics For Everyone Installing Ftk Imager Lite In Linux Command Line



2




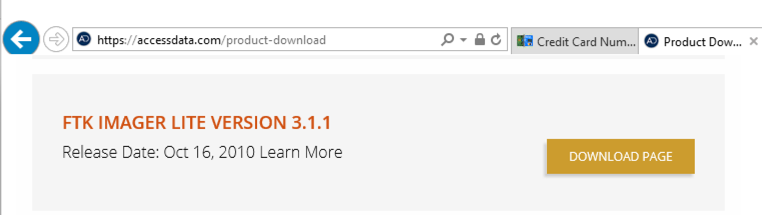
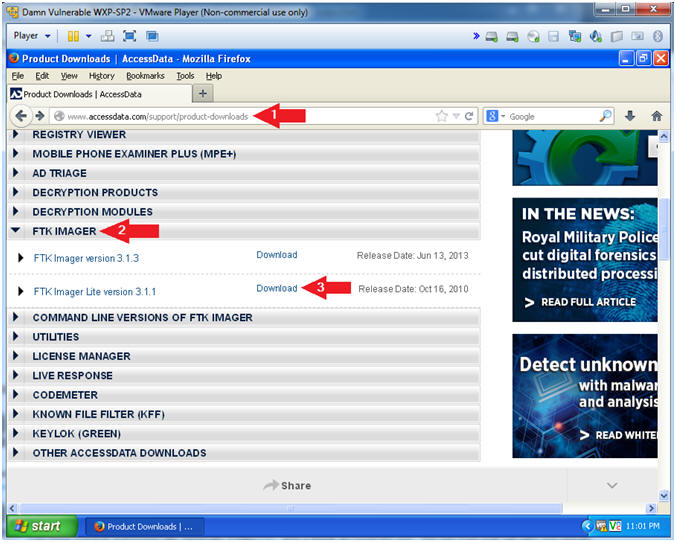
Product Downloads Accessdata



1




How To Guide Image A Hard Disk Using Ftk Imager Pdf Free Download



2



2



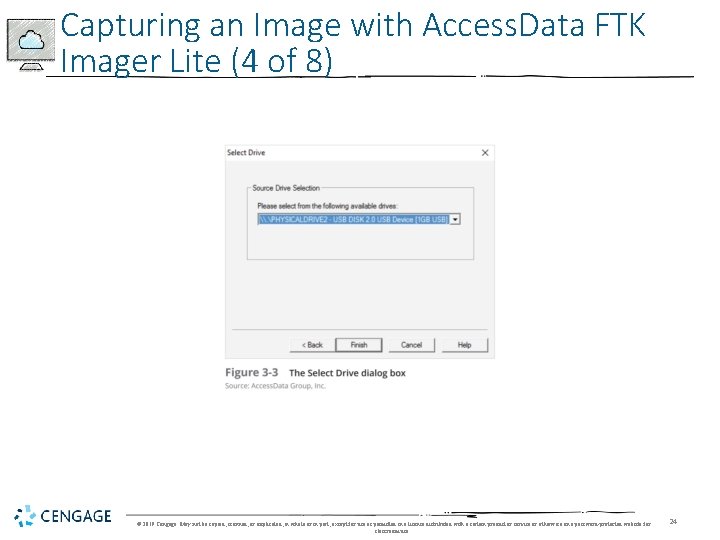
Project 3 Capturing A Ram Image 15 Points




Product Downloads Accessdata




Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna



Guide To Computer Forensics And Investigations Sixth Edition




Using Ftk Imager On Cli Challenging New Disks Technologies Cybrary




Ftk Imager Command Line Physical Disk Hashing Youtube



Pdfcoffee Com




Portable Version An Overview Sciencedirect Topics



Project 3 Capturing A Ram Image 15 Points
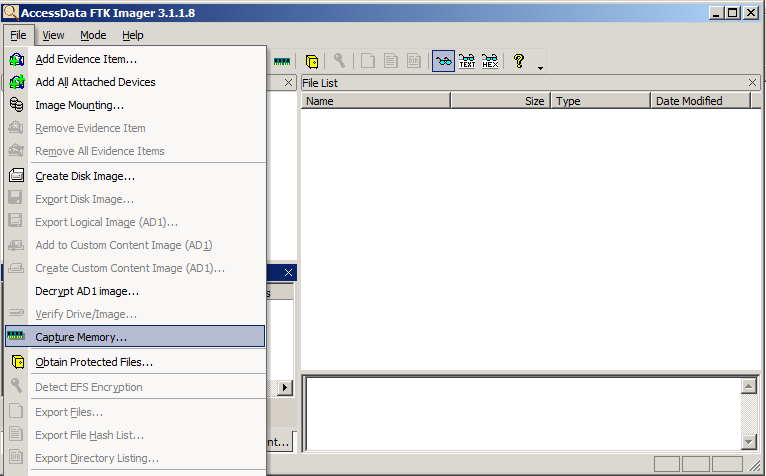



Project 3 Capturing A Ram Image 15 Points




Using Ftk Imager To Create A Disk Image Of A Local Hard Drive 1337pwn
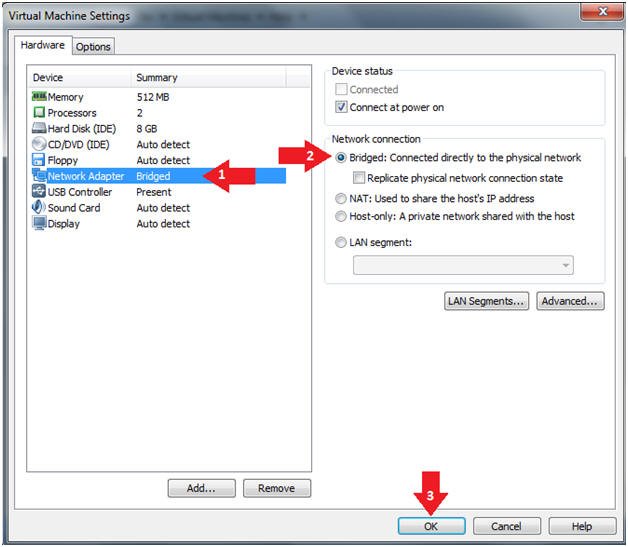



Ftk Imager Lite Lesson 1 Create Ftk Imager Lite Iso With Doiso
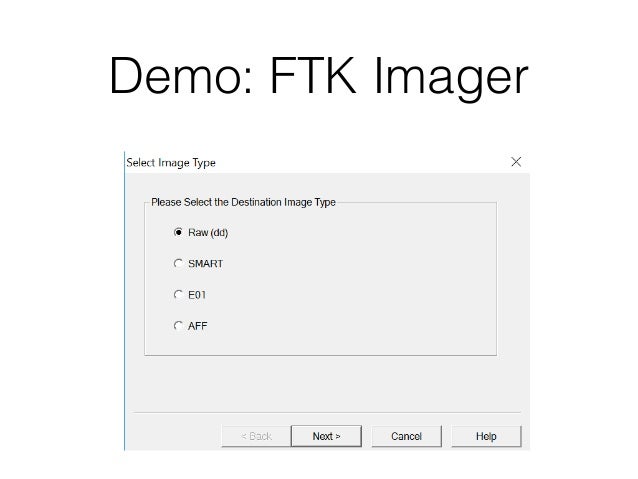



Cnit 121 8 Forensic Duplication




How To Create A Forensic Disk Image With Ftk Imager On Windows Youtube




Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna




Forensic Report Sample Volatile Memory Acquisition Using Ftk Imager Lite By Vishal Thakur Medium




Forensic Disk Images Of A Windows System My Own Workflow Andrea Fortuna




How To Guide Image A Hard Disk Using Ftk Imager Pdf Free Download



2
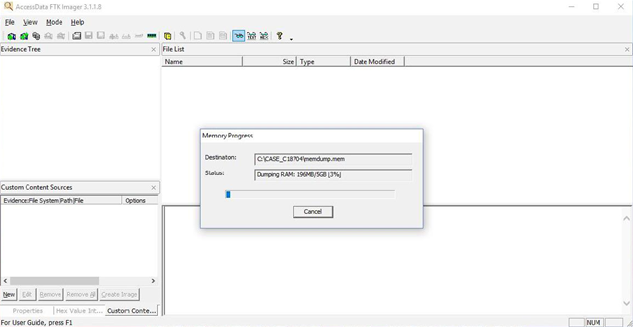



Forensic Report Sample Volatile Memory Acquisition Using Ftk Imager Lite By Vishal Thakur Medium
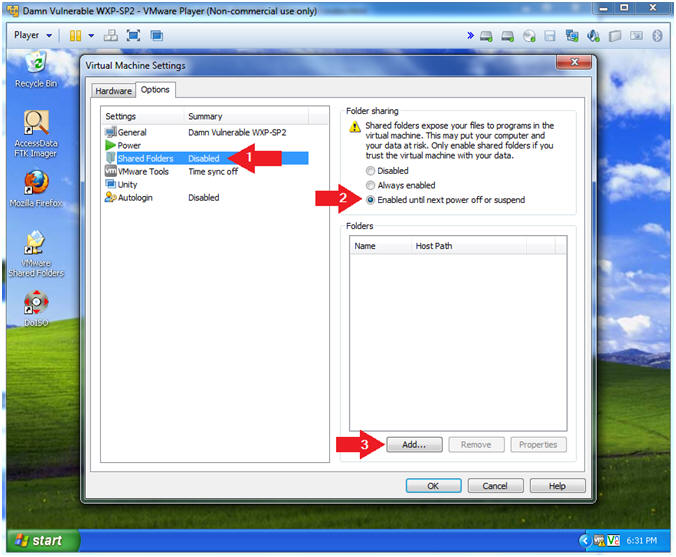



Ftk Imager Lite Lesson 1 Create Ftk Imager Lite Iso With Doiso



No comments:
Post a Comment